This is a very usefull feature. In 6.0, all saves can now be set to "Published: no". This will cause saves to only be visible for editors.
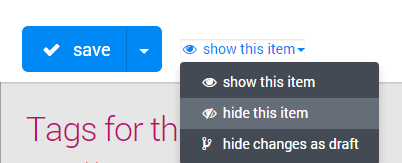 NEW in 8.5: You now have up to 3 different options, of which you will see only the appropriate ones. The options in 8.5 now are:
NEW in 8.5: You now have up to 3 different options, of which you will see only the appropriate ones. The options in 8.5 now are:
- show the item (shows everything you just edited)
- hide the item (hide the entire item even if it was published before, NEW in 8.5)
- hide changes as draft (hide only the changes you made, but keep the previous "branch" visible)
Here's how it works
- Basically an item can be published or not, and if it's not published, then the end-users don't see it, but editors do.
- When changing a published item but choosing to not publish the changes, a clone-item is branched and co-exists, but is hidden. This item is the one shown to editors, while end-users see the original branch.
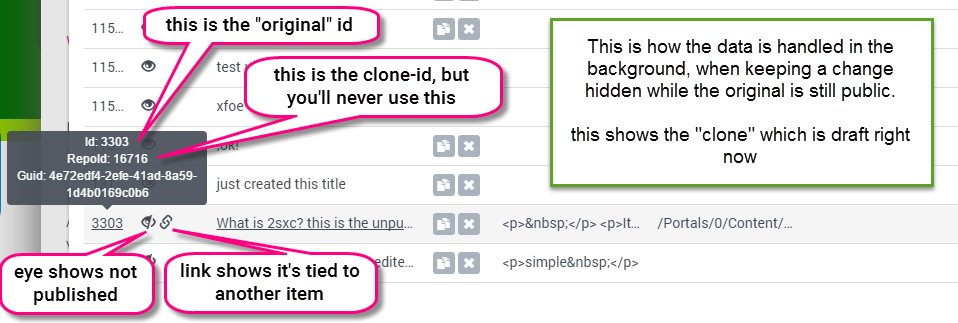
What the Template Designer must know
In the background, all is handled transparently. The templates receive the correct data based on the users Edit-Permissions.
Using Published-State in Templates
The following Tokens / Variables give your template more control
- [Content:IsPublished] will return a "true" or "false". Use this to color-mark your output like class="publish-[Content:IsPublished]"
- @Content.IsPublished has the same effect
The following Razor-Variables offer even more control
- @Content.GetDraft() -- not quite ready yet
- @Content.GetPublished() -- not quite ready yet
Have fun!
Your 2sic